About the Solution
The Solution consists of three parts, Electronic Key, Electronic Lock and Management Software. The Electronic key is the core of the system, which powers the lock when it is unlocked. Locks are passive devices. Access rights are stored in the electronic key. The Management Software is the foundation of the entire solution, by managing the software, distribution and revoking access rights and reviewing access records.
System Components

Electronic Keys
Keys are rechargeable and Multiple Key Types available, all keys have Voice Prompts and LED Indicator.
Basic Key
Bluetooth Key
Bluetooth and Fingerprint Key
4G Fingerprint and Pin Key
IP65 Rated

Electronic Locks
Locks are Powered by the key, locks have no wires or key way for object obstruction.
Various Locks
Authorized Access Only
IP68 Rated
Audit Data Locked and Unlocked
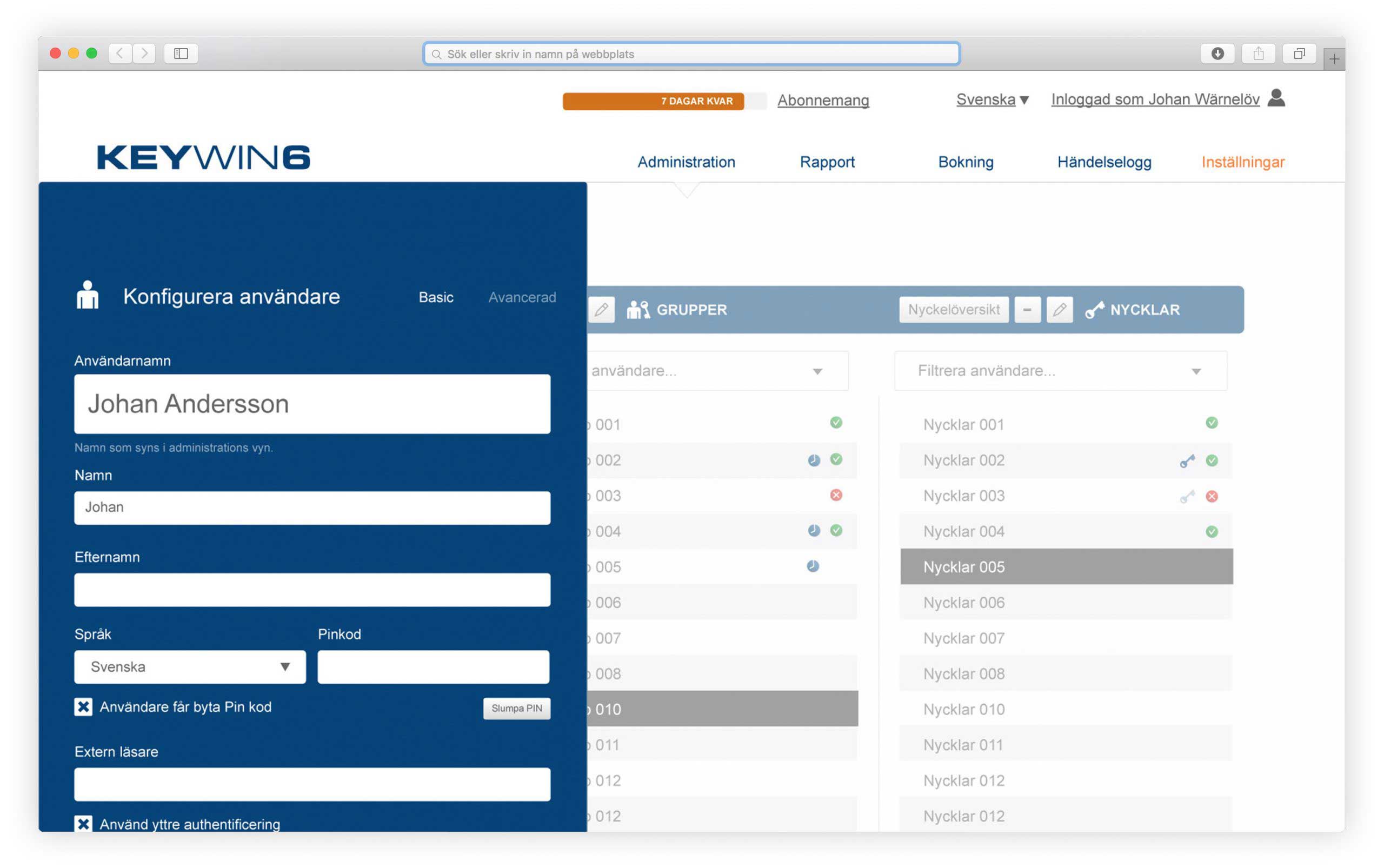
Management Software
The Software lets you Program and Control each key and lock. Creating full Audit trails, and authorizing remote job requests.
Remote Programming
Audit Trail
Hosted or Local Install
App
Overview
One Key to Unlock Multiple Locks
A single key can unlock multiple locks and create a full audit trail
Access Control
Through the Management Software, access rights can be set at any time and day, as well as specific locks or areas.
Lock Event
Through the Management Software, access rights and lock events can be reviewed.
Access Records
The Management System can provide access information to all operations performed by personnel, including a complete Audit Report.
AES256 Encryption
AES256 encryption technology prevents technical unlocking, securing lock and key encryption.
Lost Key Management
In the event of key loss or theft, such keys can be swiftly disabled and blacklisted.
Easy to Install
Without power or wiring installation is simpler and cost efficient.
API Integration
Seamlessly integrate with your systems for independent customization.
Key Storage

Automatic Storage with Charging and Key Retrieval.
- Charge Keys
- User Profiles assigned to most charged key on removal
- Automatic Key Records Update for Work Day
- Remote Key Changes
In Action
- Security 100%
- Customer Satisfaction Guarenteed 100%
- Scalable Solutions 100%
Get Started
If you would like more Information or to Book a Demo, Please Contact Us